Storing Non Printable Characters In Database Security Vulnerability 1 Poor database encryption Considering your database as a backend part of your system and ignoring its security leaves it vulnerable to hacking The database has network interfaces that hackers can easily track if your software security is poor
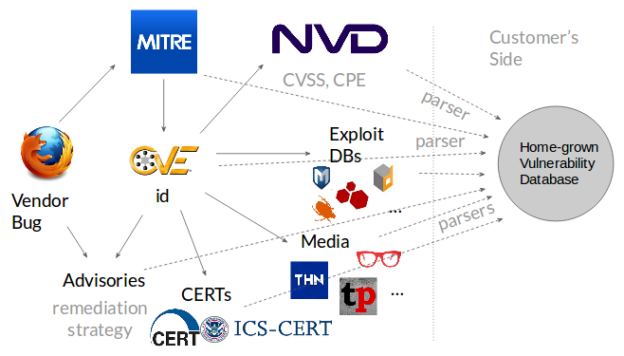
The Common Vulnerabilities and Exposures CVE program is a dictionary or glossary of vulnerabilities that have been identified for specific code bases such as software applications or open libraries This list allows interested parties to acquire the details of vulnerabilities by referring to a unique identifier known as the CVE ID Human Error Weak passwords password sharing accidental erasure or corruption of data and other undesirable user behaviors are still the cause of almost half of data breaches reported Exploitation of Database Software Vulnerabilities
Storing Non Printable Characters In Database Security Vulnerability
 Storing Non Printable Characters In Database Security Vulnerability
Storing Non Printable Characters In Database Security Vulnerability
https://i0.wp.com/confamtips.com/wp-content/uploads/2020/09/vulnerability-database.png?resize=1024%2C536&ssl=1
This in an old question but it deserves a new answer use UTF 8 Browsers databases and web servers now all support UTF 8 encoding which means that you don t have to encode special characters except as discussed here and
Pre-crafted templates use a time-saving service for creating a varied series of files and files. These pre-designed formats and designs can be utilized for numerous individual and expert tasks, consisting of resumes, invites, flyers, newsletters, reports, discussions, and more, simplifying the content development process.
Storing Non Printable Characters In Database Security Vulnerability
Security Vulnerability Notice Meltdown And Spectre Microprocessor

How Not To Get Hacked A Guide For WordPress Website Developers And

Yet Another Security Vulnerability Afflicts Indias Citizen Database

BREAKING NEWS WordPress Security Vulnerability In All WordPress Sites

Database Vulnerability Scanning In Atlanta GA

What Is A Security Vulnerability Official Juniper Networks Blogs

https://cheatsheetseries.owasp.org/cheatsheets/SQL_Injection_Prevention
To avoid SQL injection flaws is simple Developers need to either a stop writing dynamic queries with string concatenation and or b prevent user supplied input which contains malicious SQL from affecting the logic of the executed query

https://nvd.nist.gov/vuln/detail/CVE-2019-1084
An information disclosure vulnerability exists when Exchange allows creation of entities with Display Names having non printable characters An authenticated attacker could exploit this vulnerability by creating entities with invalid display names which when added to conversations remain invisible

https://www.shrm.org//Pages/Top-Database-Security-Threats.aspx
Assessing for any database vulnerabilities identifying compromised endpoints and classifying sensitive data Managing user access rights and removing excessive privileges and dormant users
https://access.redhat.com/security/vulnerabilities/RHSB-2021-007
The cat command provides the A and v flags to visualize non printable characters thus making the presence of BiDi control sequences known Acknowledgements Red Hat acknowledges Nicholas Boucher and Ross Anderson of University of Cambridge for responsibly reporting this issue
https://www.zdnet.com/article/the-top-ten-most-common-database
The researchers say that the top ten vulnerabilities often found in database driven systems whether during the creation phase through the integration of applications or when updating and
New Updated CVE Records cvelistV5 bulk downloads repository on GitHub includes a Releases feed of new updated CVE Records The mission of the CVE Program is to identify define and catalog publicly disclosed cybersecurity vulnerabilities This data enables automation of vulnerability management security measurement and compliance The NVD includes databases of security checklist references security related software flaws misconfigurations product names and impact metrics
CVE 2019 1084 An information disclosure vulnerability exists when Exchange allows creation of entities with Display Names having non printable characters This security update addresses the issue by validating display names upon creation in Microsoft Exchange and by rendering invalid display names correctly in Microsoft Outlook clients