Non Printable Characters Digital Forensics Printer and Scanner Forensics Abstract This chapter exhibits the technologies on device source identification and document forgery detection It presents three examples on printer identification scanner identification and document forgery detection for details
The analysis or examination phase requires the use of appropriate digital forensic tools and methods to uncover digital data There are numerous digital forensics tools on the market of varying qualities Examples of digital forensics tools include Encase FTK and X Ways Forensics This paper describes the development of a nondestructive method that is intended to detect imperceptible fraudulent alterations to digital print samples
Non Printable Characters Digital Forensics
 Non Printable Characters Digital Forensics
Non Printable Characters Digital Forensics
http://1.bp.blogspot.com/-RJoAjVg34t0/UJokUXfAVbI/AAAAAAAAAGA/C8EabSb4PG8/s1600/5.png
It discuses some general hardware HW requirements and presents methods that use forensic printed marks character glyphs and halftone images as the basis for forensic signature recovery The chapter also illustrates the potential use of forensic authentication in the context of currency protection
Pre-crafted templates use a time-saving solution for developing a varied range of files and files. These pre-designed formats and designs can be made use of for different personal and professional tasks, including resumes, invitations, leaflets, newsletters, reports, discussions, and more, enhancing the material creation procedure.
Non Printable Characters Digital Forensics
Reference Non Printable Characters List DevsDay ru
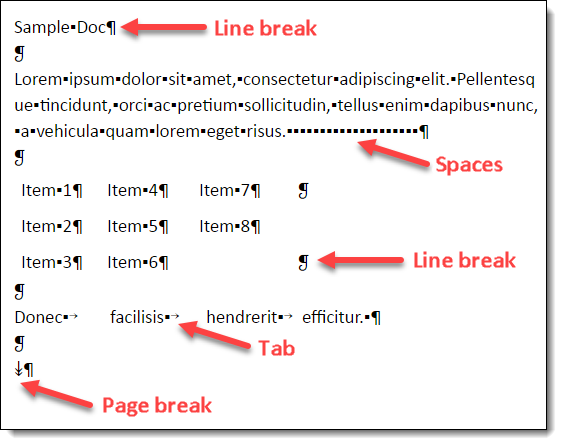
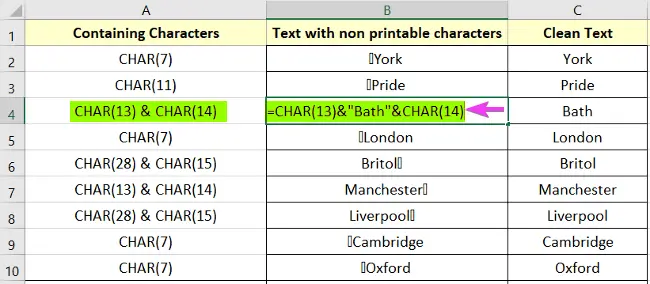
4 SAMPLE TEXT WITH NON PRINTABLE CHARACTERS SamplePrintable2
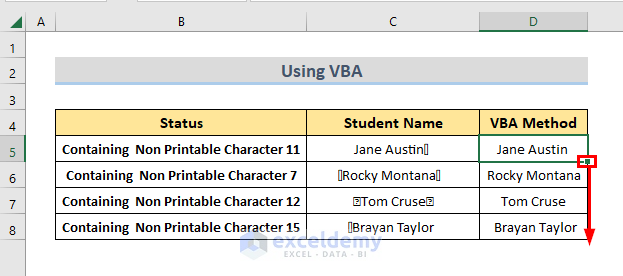
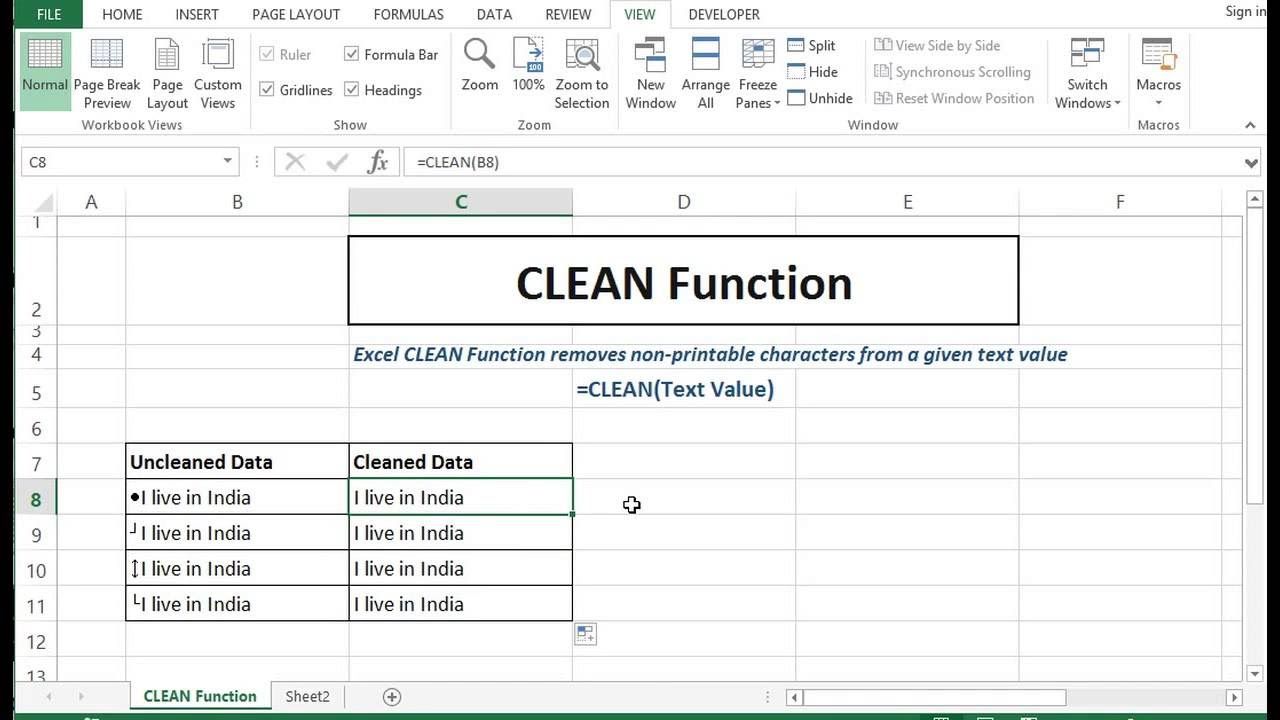
How To Remove Non Printable Characters In Excel 4 Easy Ways
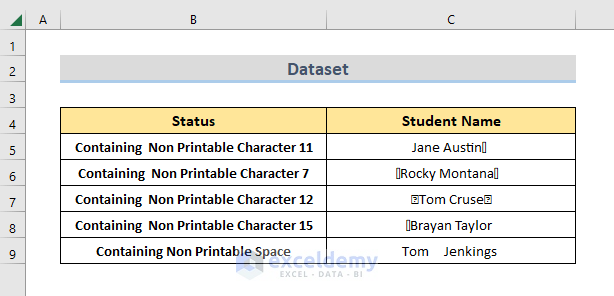
How To Remove Non Printable Characters In Excel 4 Easy Ways
Remove Non Printable Characters In Excel 5 Methods
Printable Ruler In Excel Printable Ruler Actual Size

https://dev.to/smpnjn/full-list-of-non-printable-characters-lgp
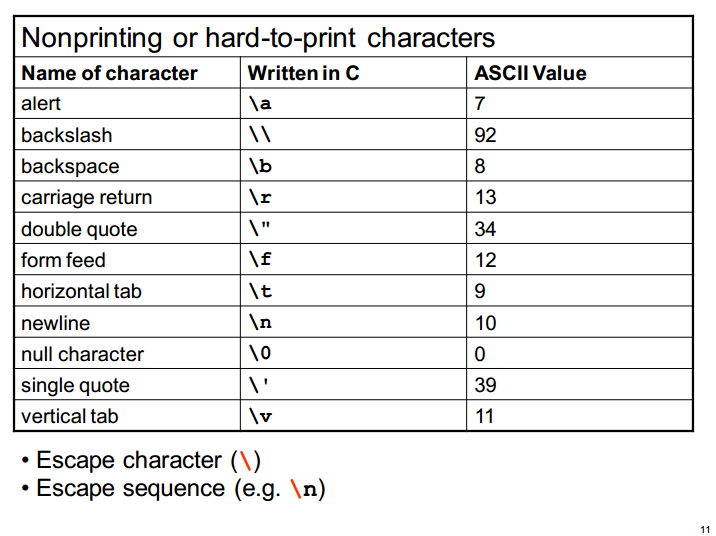
Full Non Printable Characters List Below find a list of all non printable characters along with their binary decimal and hexadecimal codes You can also find their escape sequence used in many programming languages and caret notation used with cat

https://www.experts.com/content/articles/fcohen2_fonts_for_for…
Of non printing characters and the presentation is a function of the utility for the examiner Each symbol should self indicate the underlying bit pattern that produced it so that it can be traced back to its original value

https://people.cs.umass.edu/~liberato/courses/2017-spring-compsci365/
Carving Unicode UTF 8 Not all text is ASCII Recall that Unicode maps characters to code points numbers and the various UTF schemes map code points to particular byte encodings Code points are just hex values and are often written as U XXXX where XXXX is the hex value So for example the code point for is 163 in decimal 0xa3
https://techwithtech.com/what-is-ascii
ASCII is a standard coding system that assigns numbers letters and symbols to the 256 slots in an 8 bit code you ll learn further below what 8 bit exactly is The ASCII decimal is made up of binary the language used by computers ASCII corresponds to the English alphabet

https://www.sciencedirect.com/science/article/pii/S1742287609000401
Since some filesystems are unable to represent URNs accurately e g Windows has many limitations on the types of characters allowed for a filename the Directory Volume encodes URNs according to RFC1738 Berners Lee et al 1994 non printable characters are escaped with a followed by the ASCII ordinal of the character
Digital forensics for printed character source identification Abstract Even digital content is widely used nowadays printed documents are still ubiquitously accepted and circulated Therefore identifying the printed character source is essential for criminal investigations to authenticate the digital copies of the printed documents This research engages in the forensic study for printed document source identification This study has investigated the scanned and microscopic images in printed source identification by feature based SVM classification system and
CSAFE co director Hal Stern and his team conducted a study to investigate this problem using 123 participant signatures The goal was to determine if more complex signatures affected the way an examiner makes comparisons Researchers found the answer to be yes